Course 11 - Cloud Incident Response
Incident response in the cloud requires fast action because attackers
can modify cloud resources quickly. Cloud providers offer tools that
help teams detect respond to and recover from attacks.
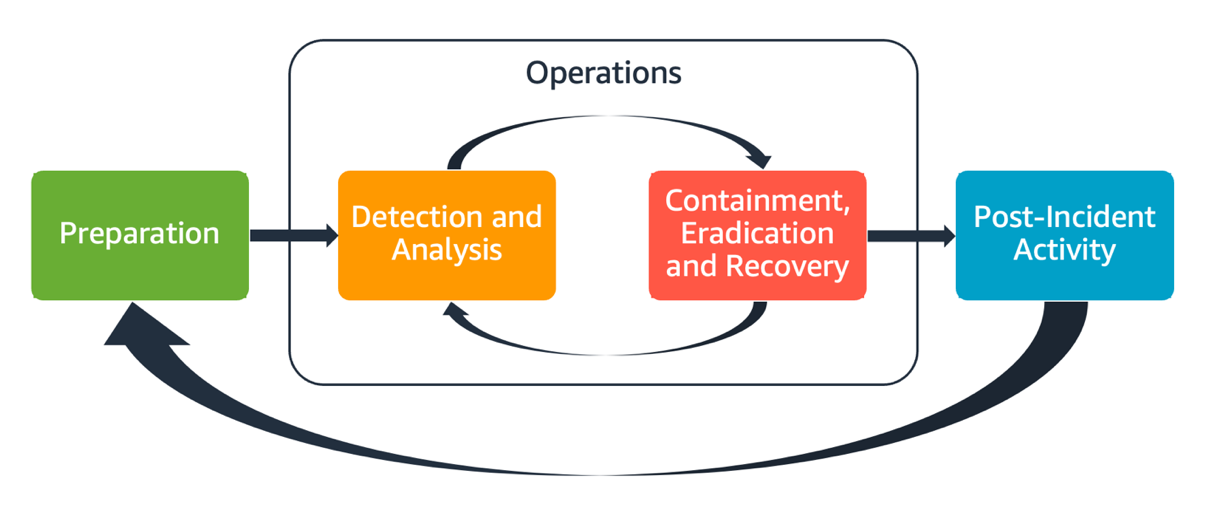
Key Concepts:
-
Detection: Detection uses cloud
monitoring tools to identify suspicious activity such as unusual
login attempts or unexpected network traffic. These tools review
logs and alert security teams when something appears abnormal.
-
Containment: Containment stops the
threat from spreading. This can involve disabling a compromised
account isolating a virtual machine or tightening security group
rules. Quick containment prevents further damage.
-
Investigation: Investigation uses
logs snapshots and historical data to understand how the incident
happened. Cloud platforms record most user and system actions which
helps analysts reconstruct the attacker’s steps.
-
Recovery: Recovery restores systems
and strengthens them to prevent the same type of attack in the
future. This may include rotating keys rebuilding systems or
updating security settings.


